CERTIFICATION
& AUTHORITY
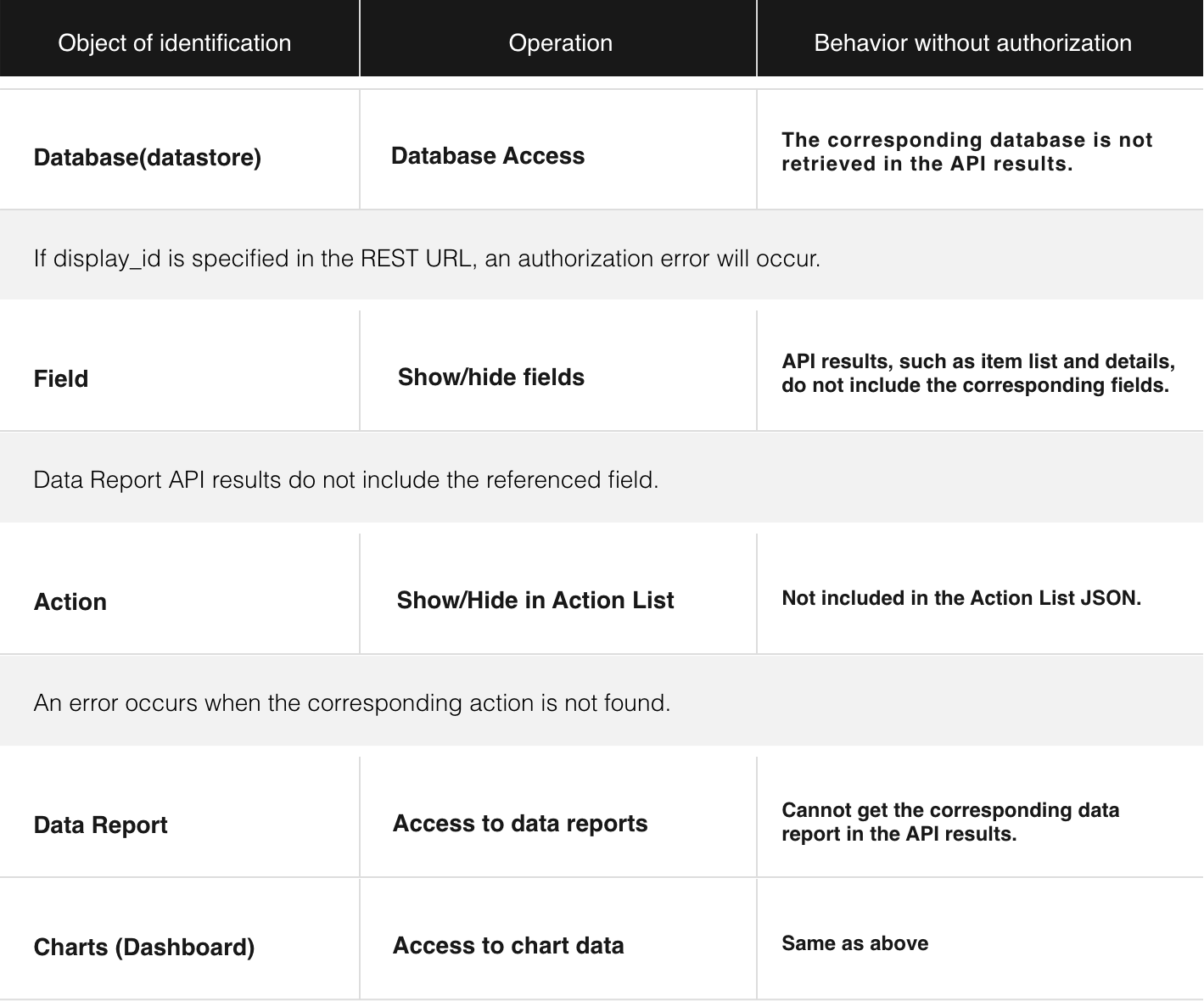
Automatically filter API return values within the scope of privileges held by the logged-in user
All data registered in Hexabase is controlled for viewing by each record within the range of privileges of the logged-in user, and is automatically filtered according to the settings without the API user’s awareness.
In most cases, enterprise systems require security controls based on the authorization level of the logged-in user.
Hexabase automatically filters API return values according to user, group, and role settings.
Hexabase Authentication and Authorization Features
01
Access key
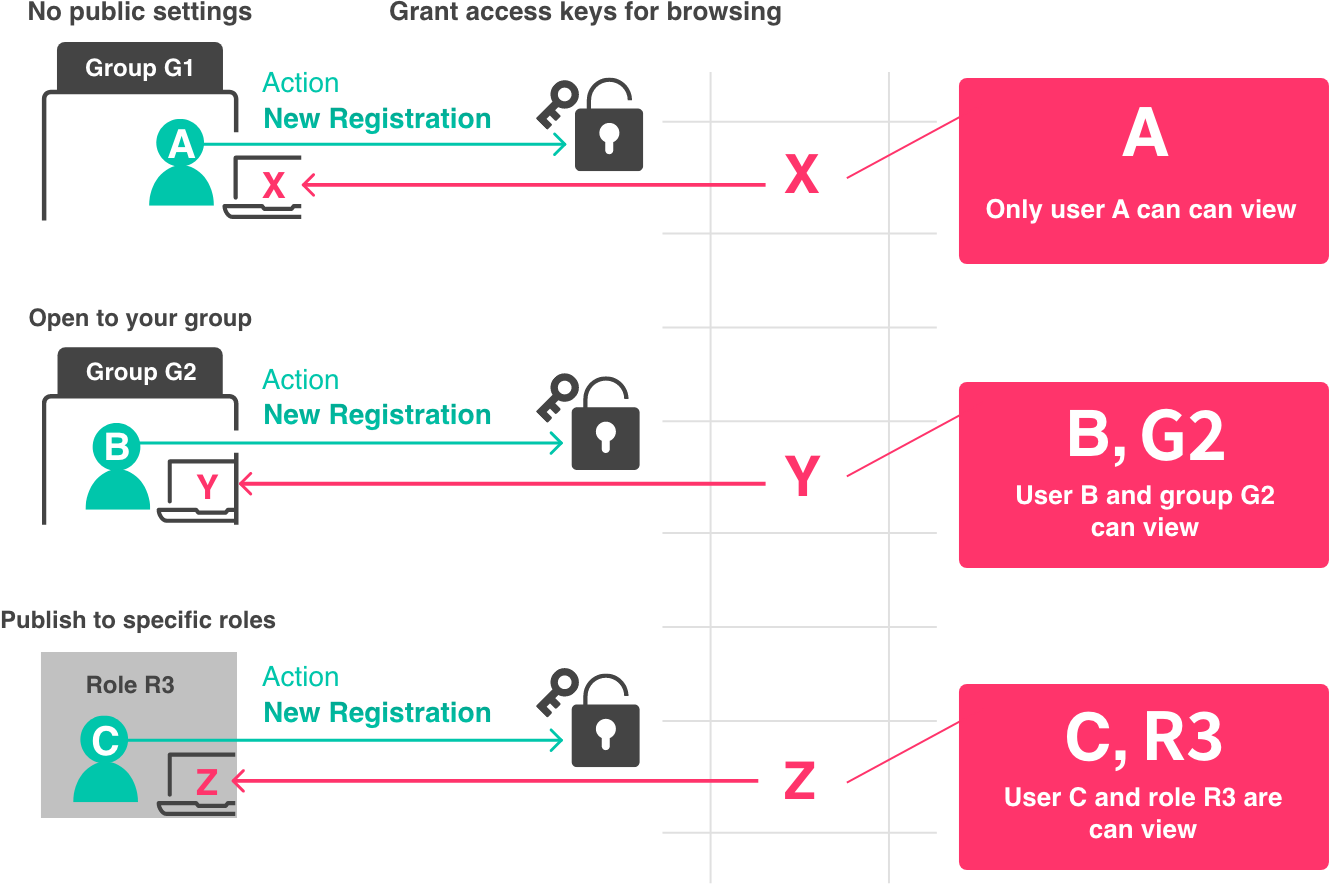
Each record row in the database can be controlled to be viewable/unviewable.
The access key is an identifier to control the item’s viewing privileges. There are two types of access privileges: authorization access keys (keys) held by users, groups, and roles, and browsing access keys (keyholes) held by items. Then, whether or not the item can be viewed is determined based on whether or not the authorization access key and the viewing access key match.
02
Authority by role
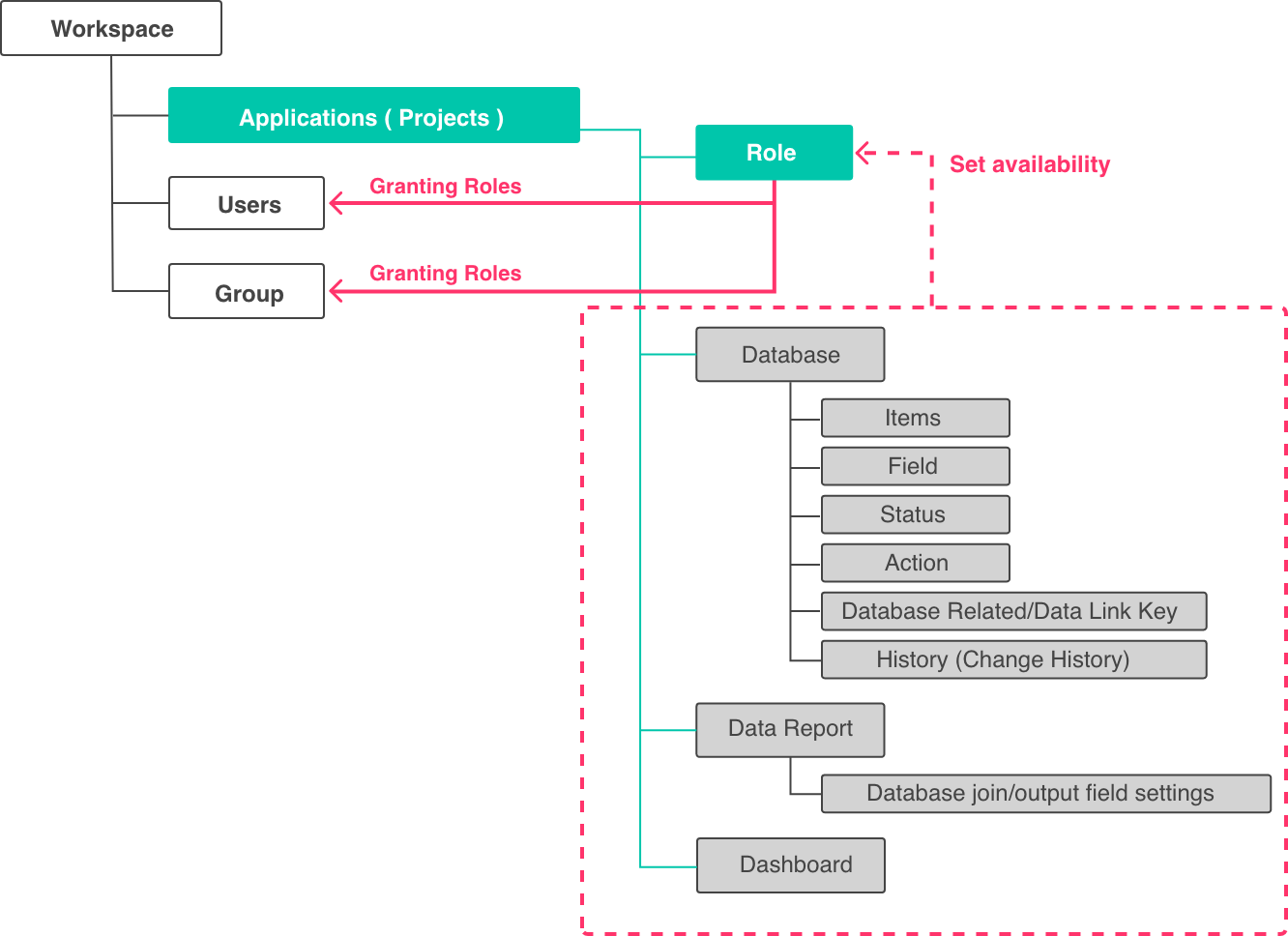
Roles” are the privileges that a user has for each functionality in the application (database, fields, actions, etc.) Hexabase assigns available roles to each functionality.
A user group is granted a role to use a feature.
03
Roles are controlled by groups to control the scope of application
Users and groups belong to workspaces, and roles belong to applications; in Hexabase system development, each function of an application sets availability for roles and grants roles to users and groups.
When a role is granted to a group, the role is inherited down to the lower groups. By default, the members role is granted to the top level “workspace” group.